Overview
We can all use more security in our lives, especially with cybercrime at an all time high. In this edition I will show you some simple configuration changes that you can make in Microsoft 365 that will help harden the security of your organization’s Microsoft 365 implementation.
Target Audience
The target audience for this post is anyone who is involved with administering their organizations Microsoft 365 environment or anyone who would like to learn more about Microsoft 365 Administration and Security.
Microsoft 365 Components
- Microsoft Office Suite (Word, Excel, PowerPoint, Outlook, Etc)
- Microsoft Exchange (Email Server)
- Microsoft SharePoint (team site/online file management)
- Microsoft Teams (team collaboration and Voice over IP or VoIP services, Microsoft Shifts for team time and scheduling)
- Microsoft Entra ID (Identity and Access Management or IAM) for managing user accounts and guest access
- Microsoft Azure (Compute Resources/Virtual Machines, Platform as a Service or PaaS, Infrastructure as a Service or IaaS)
- Microsoft Power Platform (visual code programming, workflow management, Power Automate formally known as Microsoft Flow)
- Microsoft Engage, formally known as Dynamics 365 (Customer Relationship Management or CRM)
- Microsoft Planner (project and task management)
- Microsoft Forms (for custom Internet facing web forms, can be integrated with Power Automate for workflow management)
- Microsoft Lists (formally known as SharePoint lists) which can also be integrated with Power Automate for workflow management)
- Microsoft Bookings (similar to calendy or other personal booking page sites)
- Microsoft Stream (much like a corporate youtube)
- Microsoft Whiteboard (can be used during a Microsoft Teams meeting to collaborate with others)
- Microsoft 365 Admin Center (portal to access all other functional area admin portals such as Teams Admin, SharePoint Admin, Entra ID, Etc.)
- Microsoft Security Center (for threat management, quarantine management, etc.)
- Microsoft Compliance Center (for eDiscovery, Compliance Policy Management, Data Loss Prevention, Etc.)
Introduction
With how far Microsoft 365 has grown since its inception, with all the bells and whistles it now has, the touchpoints for vulnerabilities and the risk of exposure of critical company data makes security of the utmost importance. Over the years Microsoft has made some great out of the box improvements such as the integration of security defaults, which with new Microsoft 365 implementations, are on by default and will force users to configure multi-factor authentication within 14 days of the account being signed in for the first time. Microsoft 365 has some impressive security features under the hood that can even be extended to other web applications using SAML for Single Sign-on or SSO for short.
Overview of the Microsoft 365 Admin Center
Multi-factor Authentication (MFA)
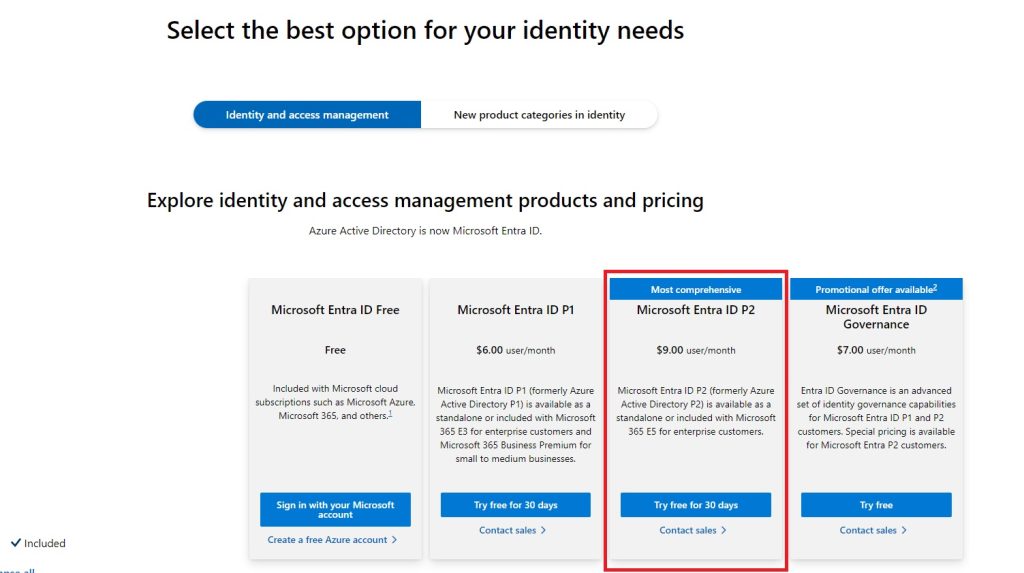
There are a few methods available for foolproofing MFA in Microsoft 365. The first of the two methods is security defaults, which I mentioned briefly above. If your Microsoft 365 tenant was implemented before February of 2020, then it is possible that Security Defaults is not turned on in your implementation. The second method for foolproofing MFA is by using Conditional Access. If you are a non-profit, like many churches, Microsoft donates 10 Microsoft 365 Business Premium licenses, which makes Conditional Access available to you. If you are not a non-profit, you will need either a Business Premium license, an E3 enterprise license or higher, or an Entra ID Premium P2 license to use this feature.
Configure Security Defaults
- From the Microsoft Admin Center, click on Show all to view all settings and admin centers.
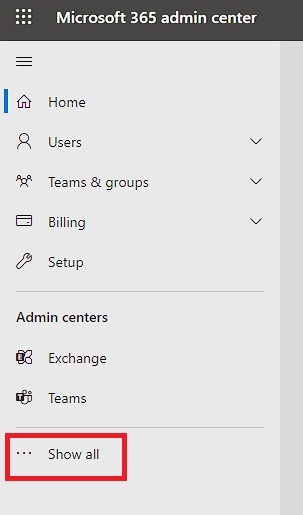
2. Click on Identity to open the Entra ID Admin console
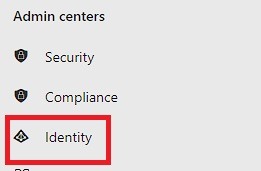
3. Click on Properties as shown below
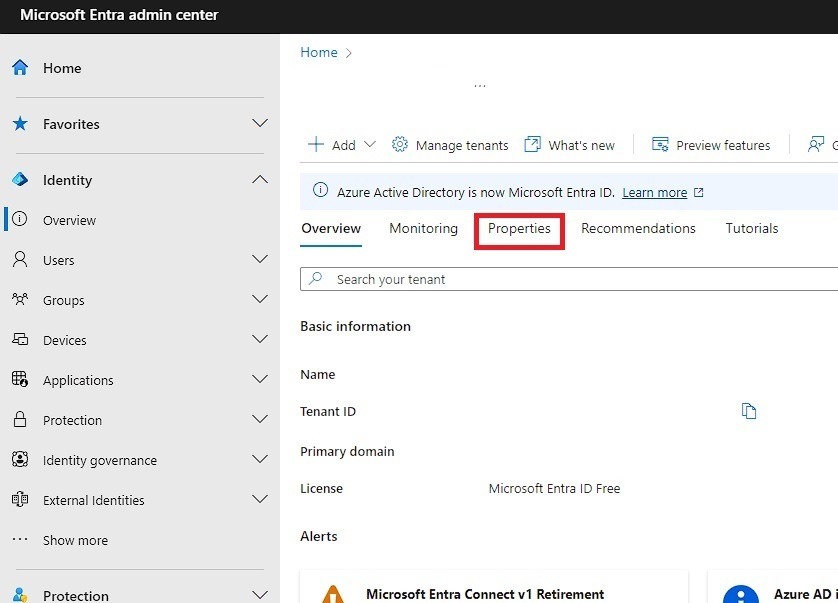
4. Click Manage Security Defaults
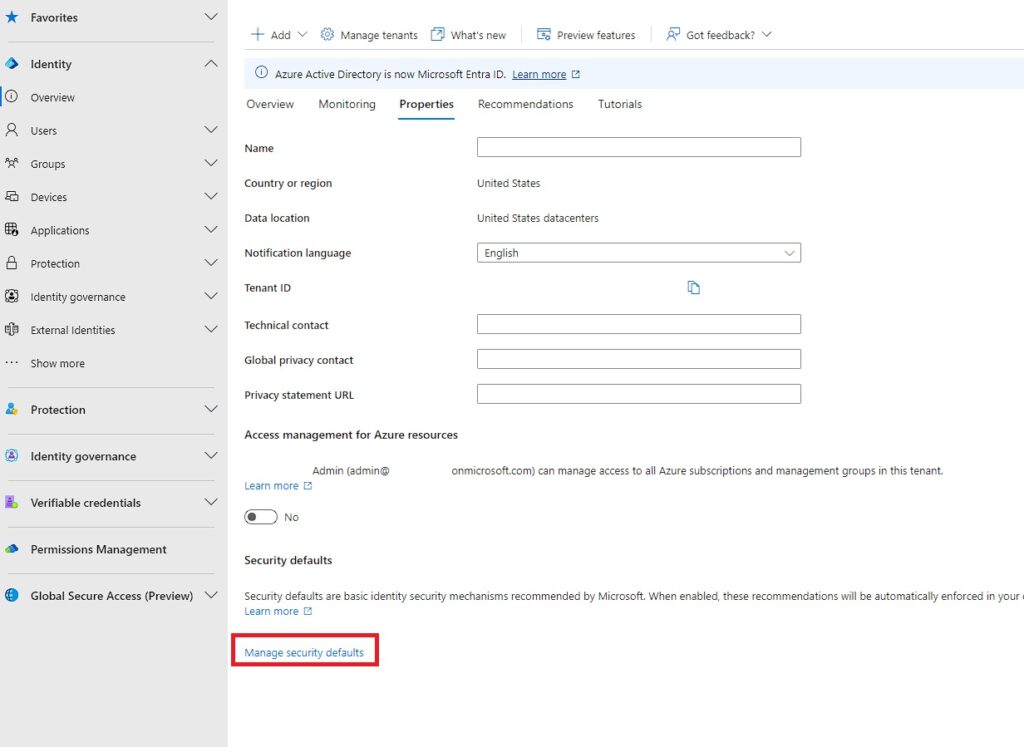
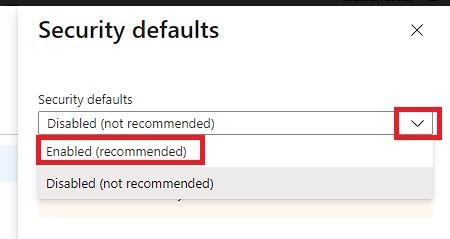
5. Choose Enable Security Defaults from the drop down menu and save the settings
Conditional Access
If you have either of the following licenses, you have the ability to use Conditional Access. Conditional Access can be used to harden the security of your Microsoft 365 implementation in many ways. You can use CA to force MFA for every login whether it is enforced on the users account or not. You can also use CA to geofence where your users can login, for instance, you can lock users down to your office if you do not want them logging in outside of work and you can also lock users down to certain countries. The true power of CA comes by combining its use with Microsoft’s Mobile Device Management system (Intune). When used with Intune, you can remove the need to geofence and simply make Intune device enrollment and compliance a requirement to allow login.
Required License
- Microsoft 365 Business Premium
- Microsoft 365 E3 or Microsoft 365 E5
- Microsoft Entra ID P2 (only required if you don’t have one of the licenses mentioned above, this would be a good option if you have Microsoft 365 Business Basic, if you have Microsoft 365 Business Standard, you are better off upgrading to Business Premium)
Enforce MFA with CA
- Login to the Microsoft Azure Portal (https://portal.azure.com)
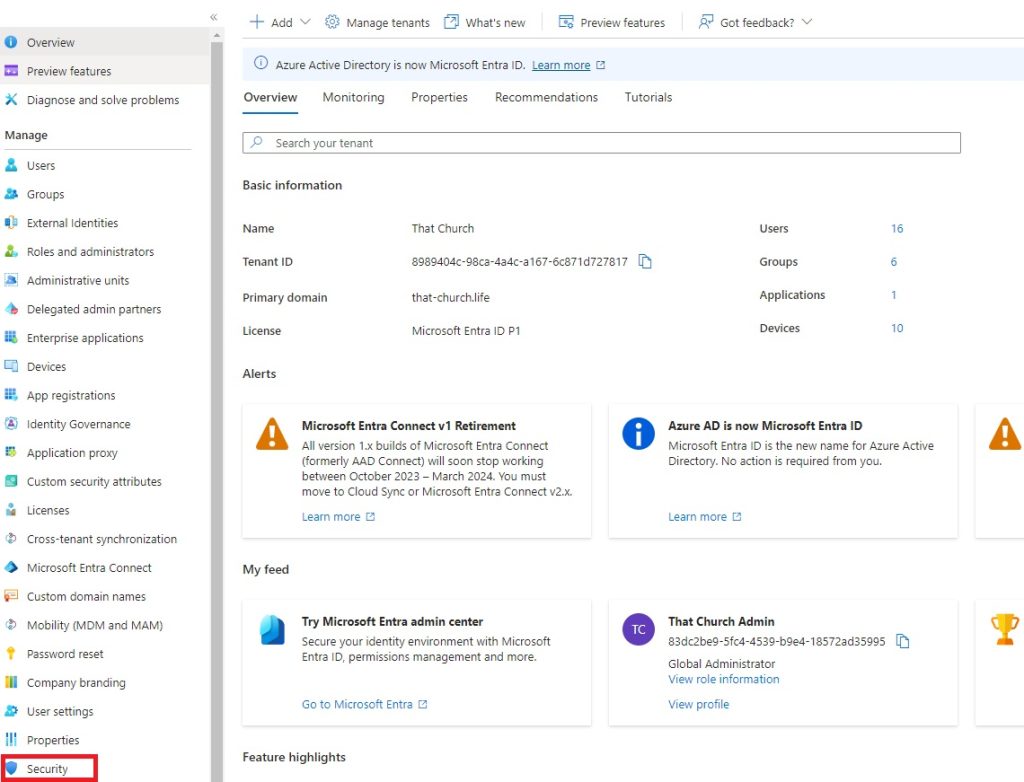
- On the left navigation bar, click on Security
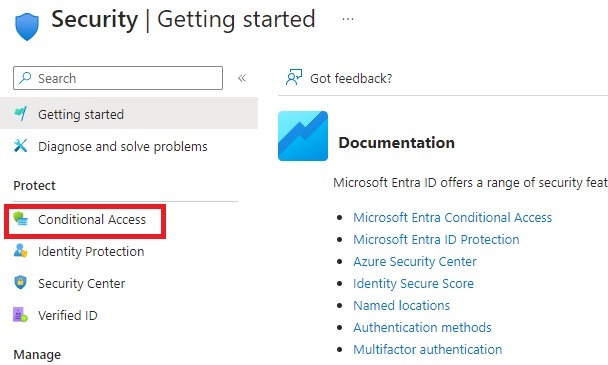
3. Click Conditional Access
4. Click Create new policy
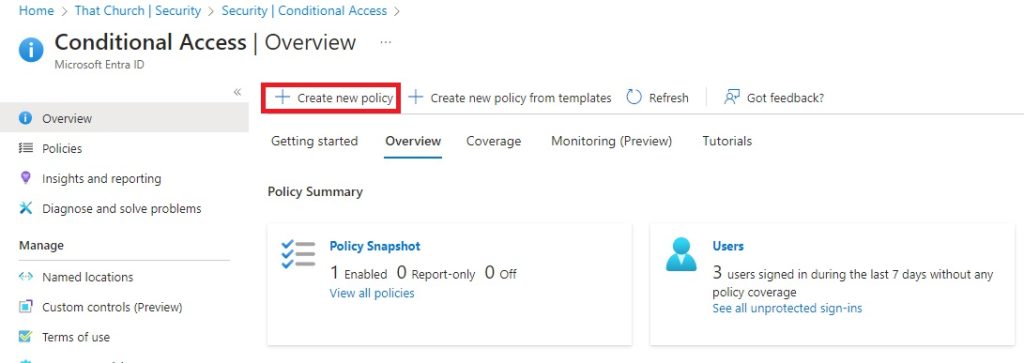
5. Give it a descriptive name and then click “Users “0 users and groups selected” and Select All Users
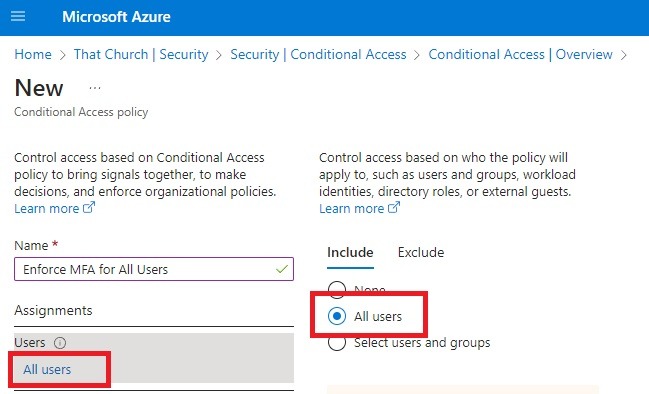
6. Next under Target resources, select All cloud apps
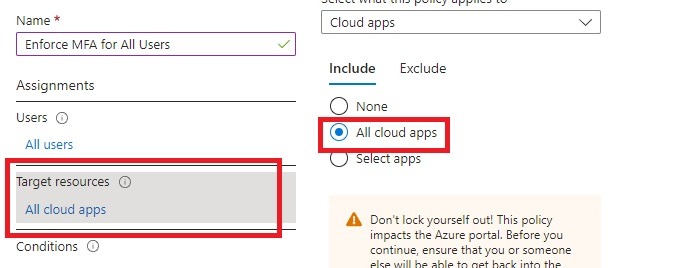
7. Under conditions, under device platforms, set configured to Yes and select any device
8. Under Locations, set configured to yes and select any location
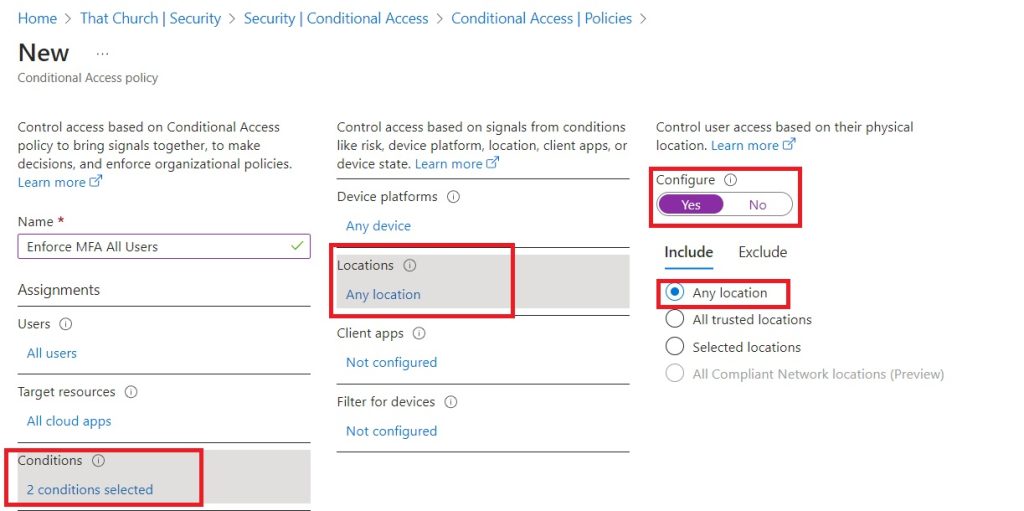
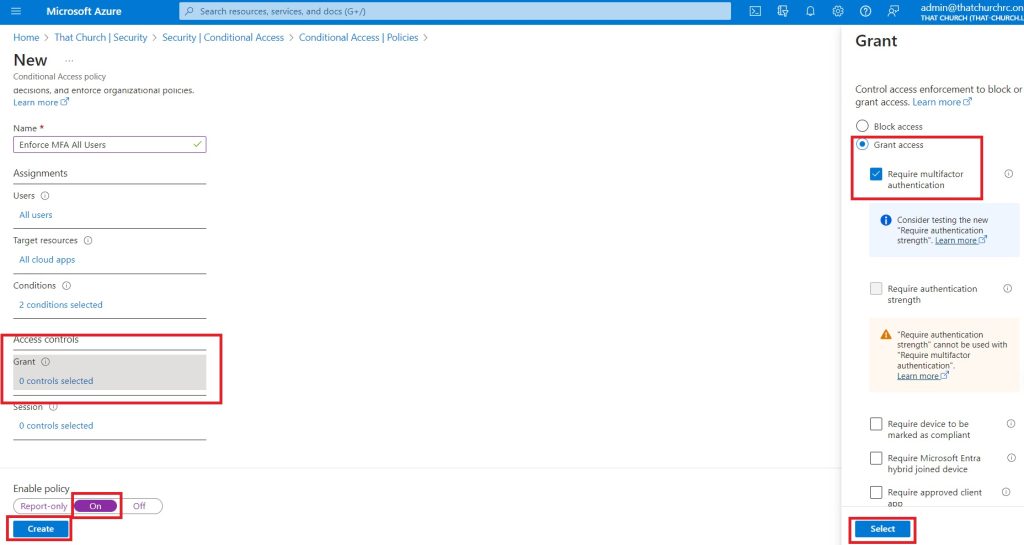
9. Under Access Control, select Grant, choose Grant Access and check the box to require multifactor authentication. Once done, set from report to On and click create.
Prevent Exfiltration
Disable Automatic Forwarding
- Go to https://security.microsoft.com and login with a global administrator account
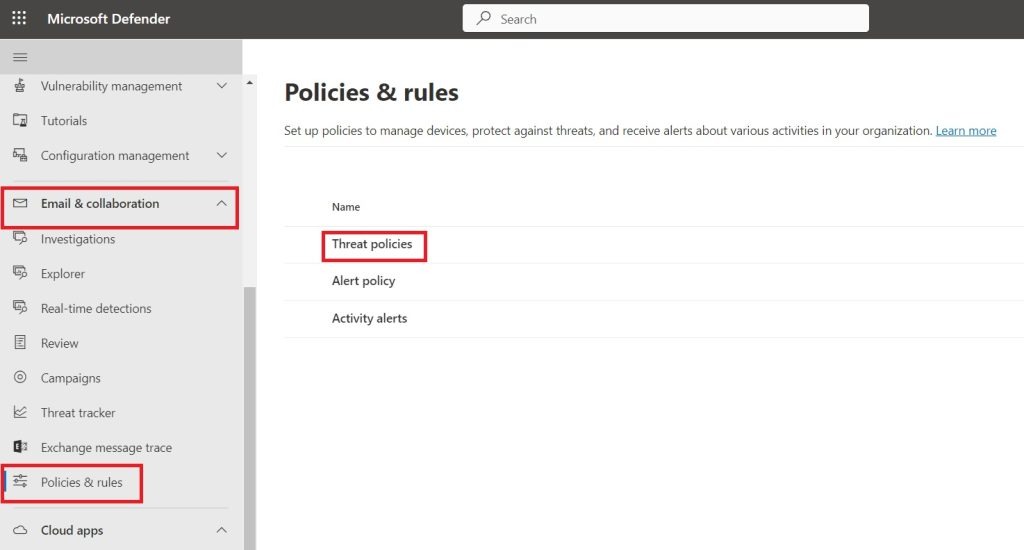
- Under email and collaboration, select Policies and Rules > Threat Policies
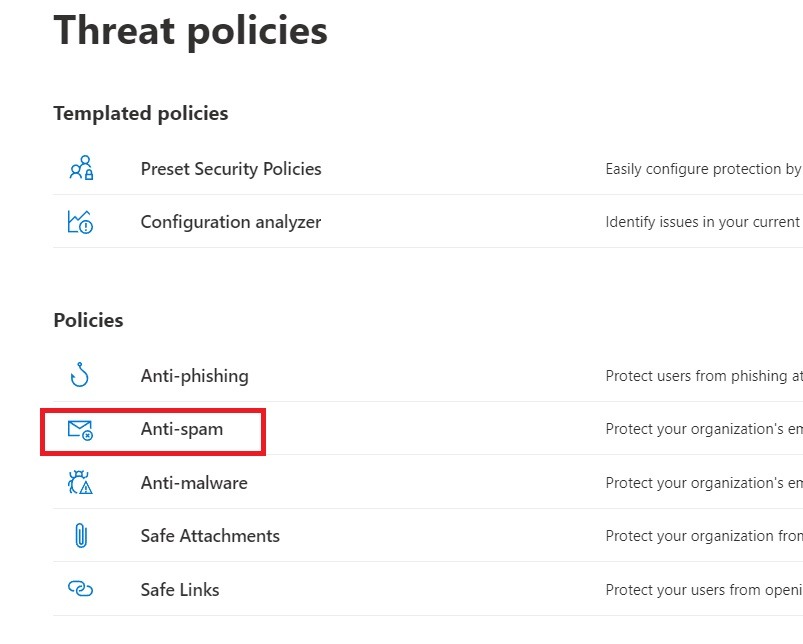
3. Click Anti-Spam under Policies
4. Click on Anti-spam Outbound Policy and click Edit protection settings
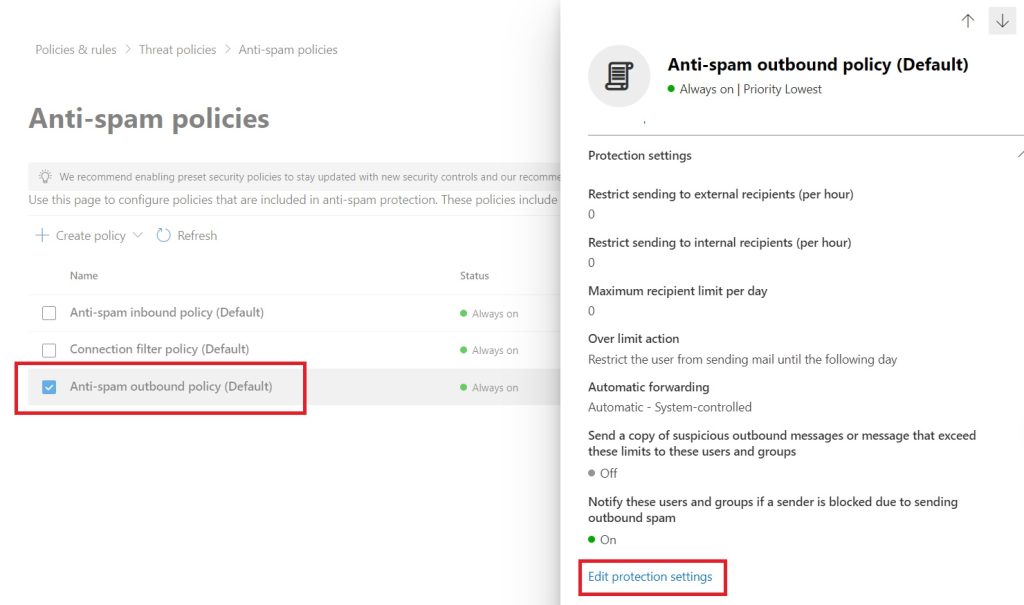
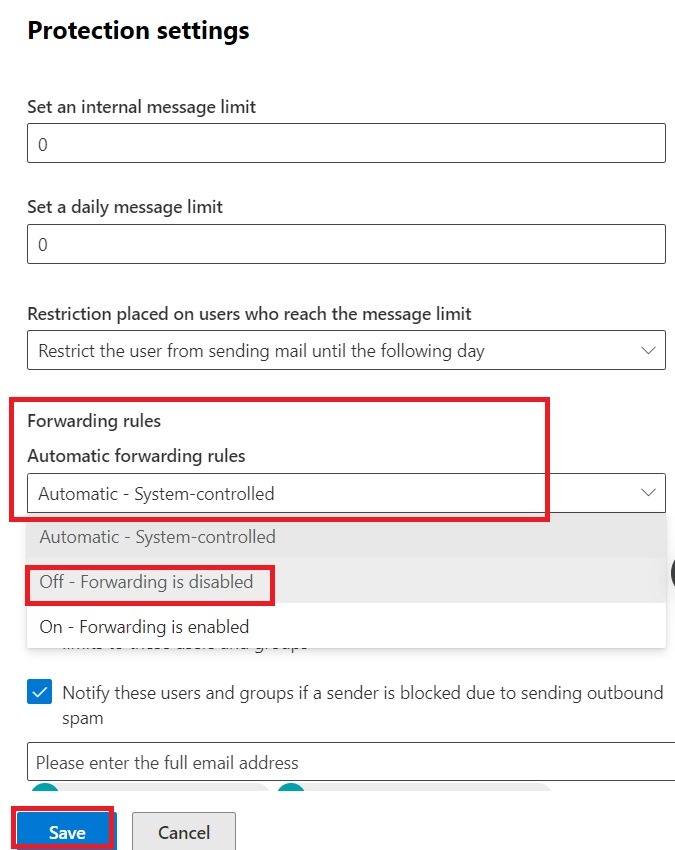
5. Under Forwarding Rules, from the drop down box, select “Off – Forwarding is Disabled” and click Save
Security Score
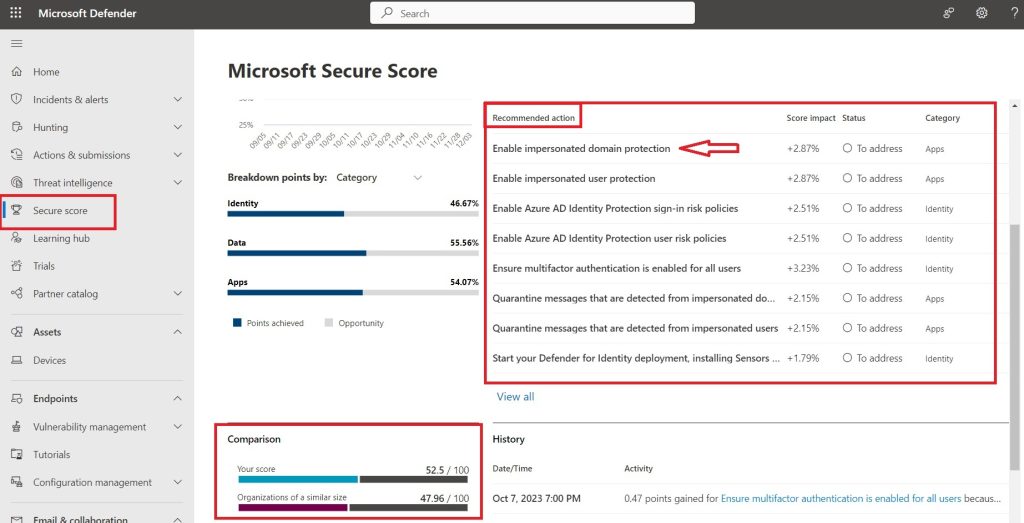
The security score dashboard is another resource you can use to harden security. Microsoft includes links to how-to articles on how to complete the checklist items. You can access it from https://security.microsoft.com (same portal used in the previous section to disable automatic forwarding). You simply click on Secure Score as shown below. If you scroll down you can see how your score compares to other organizations your size. You should at least aim to get your score above 50%. You can do this by clicking on the items in the list under Recommended Action.
Summary
To harden the security of your Microsoft 365 implementation and to raise your security score, below is a summary of the above mentioned actions that you can take to improve the security posture of your Microsoft 365 implementation.
- Ensure Security Defaults are on
- Enforce MFA for all users for all logins, from any device and any location
- Disable automatic forwarding (prevents users from configuring email to forward to an external email address) which prevents exfiltration
- Review the Security Score dashboard for recommended actions, aim for a score higher than 50%



